Sheetloom Security Document
1. Introduction
The Sheetloom Security Document provides a comprehensive overview of the security measures and controls implemented to protect Sheetloom. As a service that enables businesses to automate and manage complex Excel workflows, Sheetloom prioritizes the confidentiality, integrity, and availability of customer data.
Our platform leverages AWS services to ensure robust security and compliance with industry standards. This document outlines the specific security practices we employ to safeguard customer data, maintain system integrity, and ensure compliance with regulations such as GDPR.
Key components of our security strategy include:
- Data Protection: Ensuring the security of customer spreadsheets and associated data through encryption and access controls.
- Identity and Access Management: Implementing strict IAM policies to enforce tenant isolation and least privilege access.
- Network Security: Utilizing AWS VPCs and security groups to protect our infrastructure from unauthorized access.
- Monitoring and Logging: Employing AWS CloudWatch and CloudTrail to monitor system activity and detect potential security incidents.
- Incident Response: Maintaining a structured incident response plan to quickly address and mitigate security threats.
This document serves as a guide for our development and security teams, as well as a resource for auditors and stakeholders to understand our security posture.
2. System Overview
Purpose:
This provides a high-level description of Sheetloom, its architecture, and the AWS services used to ensure a clear understanding of the system's structure and security integrations.
Components:
- Application Description: Sheetloom is a multi-tenant application designed to automate the population of Excel spreadsheets with company-specific data. It integrates various data sources, including CSV files, databases, APIs, and websites, to ensure accurate and efficient data management and reporting.
- Deployment Models: Sheetloom supports two deployment models: a multi-tenant cloud-hosted model where multiple tenants share infrastructure, and a customer-hosted (on-premises) model where Sheetloom is deployed in the customer's own AWS account for enhanced isolation and control.
- Architecture Overview: The system architecture integrates multiple AWS services to ensure scalability, security, and high availability.
- AWS Services Used: The application leverages a range of AWS services, including AWS Amplify for frontend hosting, AWS Cognito for authentication, Amazon S3 for data storage, AWS Lambda for serverless compute, AWS Glue for data processing, Amazon Athena for data querying, API Gateway for API management, Amazon RDS for relational databases, AWS Secrets Manager for managing sensitive information, Virtual Private Cloud (VPC) for network isolation, Elastic Container Registry (ECR) for container image storage, and AWS EventBridge for automated deployment updates.
2.1 Application Description
Sheetloom Key functionalities include:
- Automated Data Integration: Seamlessly connects to multiple data sources such as CSV files, PDFs, databases, APIs, and websites to gather and consolidate data.
- Multi-Tenancy Support: Ensures that each tenant (company) operates within an isolated environment, maintaining strict data segregation and security.
- User-Friendly Interface: Provides an intuitive interface for users to configure data sources, manage data processing tasks, and generate accurate Excel reports without requiring technical expertise.
2.2 Architecture Overview
A detailed architecture diagram and configuration of supporting AWS services is included in the 5.1 Detailed Architecture Diagram section.
The high-level architecture of Sheetloom includes the following components:
- Client Interaction:
- Users access the application via a secure web interface hosted on AWS Amplify.
- Authentication and Authorization:
- AWS Cognito manages user authentication, providing secure access based on tenant-specific user pools and identity pools.
- Data Storage:
- Each tenant is assigned a dedicated Amazon S3 bucket, ensuring secure and isolated storage of their data.
- API Layer:
- API Gateway acts as the entry point for all API requests, routing them to appropriate AWS Lambda functions that handle business logic and data processing.
- Data Processing and Analytics:
- AWS Glue performs ETL (Extract, Transform, Load) operations to prepare data for analysis.
- Amazon Athena enables tenants to perform ad-hoc queries on their data stored in S3, facilitating data-driven decision-making.
- Database Management:
- Amazon RDS Aurora PostgreSQL maintains relational databases that store application metadata, tenant information, and other critical data.
- Multi-tenant deployments use Aurora Serverless v1 with auto-scaling capabilities.
- Customer-hosted deployments use Aurora Serverless v2 (provisioned mode) with configurable capacity scaling for enhanced control.
- Secrets Management:
- AWS Secrets Manager securely stores sensitive credentials and API keys, ensuring they are accessed only by authorized services.
- Networking:
- A Virtual Private Cloud (VPC) provides network isolation, with Security Groups and Network ACLs configured to control traffic flow.
- Elastic Container Registry (ECR) hosts container images used by the application, ensuring secure and efficient deployment.
- Automated Updates:
- AWS EventBridge monitors ECR image updates and automatically refreshes Lambda functions when new container images are available, ensuring timely deployment of security patches and updates.
2.3 AWS Services Used
- AWS Amplify: Facilitates frontend hosting, content delivery, and continuous deployment, ensuring rapid and reliable delivery of web interfaces.
- AWS Cognito: Manages user authentication and authorization, supporting multi-tenancy through dedicated user and identity pools.
- Amazon S3: Provides scalable and secure data storage for each tenant, with encryption and access controls to protect data integrity and confidentiality.
- AWS Lambda: Enables serverless execution of backend logic, allowing for scalable and cost-effective processing of API requests and data operations.
- AWS Glue: Manages metadata catalog for each tenant's database, providing table definitions and column information for CSV and PDF data stored in S3, enabling structured data access.
- Amazon Athena: Enables users to run SQL queries against their uploaded CSV and PDF data, with preview functionality for validating queries before using them in stitches. Also handles table creation and deletion when tenants upload or remove CSV and PDF files.
- API Gateway: Provides the endpoints for all backend Lambda functions, serving as the central entry point for API requests.
- Amazon RDS: Used to host the web application's metadata in a relational database. Utilizes Amazon Aurora PostgreSQL (version 13.9 for multi-tenant deployments, version 15.8 for customer-hosted deployments) with Serverless v2 scaling capabilities for optimal performance and cost efficiency.
- AWS Secrets Manager: Stores metadata database credentials and connection information for Athena access.
- Virtual Private Cloud (VPC): Ensures network isolation and security, with carefully configured subnets, route tables, and security settings.
- Elastic Container Registry (ECR): Stores and manages all Lambda Docker images used by the application.
- AWS EventBridge: Enables automated Lambda function updates when new container images are pushed to ECR, ensuring deployments stay current with security patches and updates.
3. Security Objectives
Purpose:
Outlines the primary security goals for the Sheetloom application to ensure a clear focus on protecting data, maintaining system integrity, and ensuring compliance.
Components:
- Confidentiality: Protecting sensitive data from unauthorized access.
- Integrity: Ensuring data accuracy and preventing unauthorized modifications.
- Availability: Guaranteeing reliable access to the application for authorized users.
- Compliance: Adhering to relevant laws, regulations, and industry standards (e.g., GDPR).
3.1 Confidentiality
Objective: Protect customer spreadsheets, business data, and user information from unauthorized access.
Implementation:
- Multi-Tenancy Isolation (Cloud-Hosted):
- Each company accesses Sheetloom via their unique subdomain (company.sheetloom.com)
- Dedicated Cognito User Pool and Identity Pool per tenant
- IAM policies ensure tenants can only access their own S3 bucket and associated services
- Strict isolation prevents cross-tenant data exposure
- Customer-Hosted Isolation:
- Complete infrastructure isolation within customer's AWS account
- Dedicated VPC, database cluster, and S3 bucket per customer
- No shared resources with other customers or Sheetloom's multi-tenant infrastructure
- Customer maintains full control over network security and access policies
3.2 Integrity
Objective: Ensure accuracy and prevent unauthorized modifications of spreadsheets and business data.
Implementation:
- Secure API Access:
- API Gateway routes requests to appropriate Lambda functions
- Each request is authenticated and authorized before processing
- Data operations are logged for audit purposes
- Data Processing Controls:
- Spreadsheet data is processed through controlled Lambda functions
- Athena queries are scoped to tenant-specific databases
- All changes are tracked and versioned
3.3 Availability
Objective: Maintain reliable access to Sheetloom's spreadsheet automation services.
Implementation:
- AWS Infrastructure:
- Amplify hosts and delivers our frontend
- Automatic scaling for Lambda functions and API Gateway
- Multi-AZ deployment for critical services
- Resilience:
- Automated failover capabilities
- Regular backup and recovery testing
- Continuous monitoring of service health
3.4 Compliance
Objective: Meet regulatory requirements while protecting customer data.
Implementation:
- GDPR Compliance:
- Transparent data processing documentation
- Built-in data subject access rights
- Secure data transfer mechanisms
- Data minimization practices
4. Compliance Requirements
Purpose:
Detail the regulatory and compliance standards that apply to Sheetloom to ensure adherence and avoid legal repercussions.
Components:
- Applicable Regulations: GDPR, CCPA, HIPAA, PCI-DSS, etc.
- Industry Standards: ISO 27001, SOC 2, NIST, etc.
- Internal Policies: Company-specific security policies.
4.1 Applicable Regulations
- General Data Protection Regulation (GDPR):
- Overview: GDPR is a regulation in EU law on data protection and privacy for individuals within the European Union and the European Economic Area. It also addresses the transfer of personal data outside the EU and EEA areas.
- Compliance Measures:
- Data Protection: Implement robust data encryption both at rest and in transit to protect personal data.
- User Consent: Obtain explicit consent from users for data processing activities.
- Data Subject Rights: Facilitate rights such as data access, rectification, and erasure for data subjects.
- Data Processing Records: Maintain detailed records of data processing activities to ensure accountability.
- Breach Notification: Establish protocols to notify supervisory authorities and affected individuals in the event of a data breach within the stipulated timeframe.
4.2 Industry Standards
ISO/IEC 27001:
- Overview: ISO/IEC 27001 is an international standard for managing information security. It provides a framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
- Compliance Status:
- Adherence: Sheetloom complies with the controls and best practices outlined in ISO/IEC 27001 to ensure comprehensive information security management.
- Implementation: Implement policies, procedures, and controls that align with ISO/IEC 27001 standards, covering areas such as risk assessment, asset management, access control, and incident management.
- Continuous Improvement: Regularly review and update security measures to maintain alignment with ISO/IEC 27001 requirements, fostering a culture of continuous improvement.
SOC 2:
- Overview: SOC 2 is a framework for managing customer data based on five "Trust Service Criteria"-security, availability, processing integrity, confidentiality, and privacy. It is particularly relevant for service providers storing customer data in the cloud.
- Compliance Status:
- Adherence: Sheetloom adheres to SOC 2 principles to ensure the security, availability, and confidentiality of customer data.
- Implementation: Establish controls and practices that meet SOC 2 requirements, including secure data handling, system monitoring, and access controls.
- Monitoring: Continuously monitor and audit systems to ensure ongoing compliance with SOC 2 standards.
4.3 Internal Policies
- Information Security Policy:
- Purpose: Defines Sheetloom's approach to managing and protecting information assets.
- Scope: Applies to all employees, contractors, and third-party partners.
- Key Elements: Data classification, access control, acceptable use, incident response, and continuous improvement.
- Data Handling Policy:
- Purpose: Establishes guidelines for the collection, processing, storage, and disposal of data.
- Key Elements: Data minimization, encryption standards, access restrictions, and data retention schedules.
- Incident Response Policy:
- Purpose: Outlines the procedures for responding to security incidents.
- Key Elements: Incident detection, response steps, roles and responsibilities, and communication protocols.
5. Architecture and Components
Purpose:
Provide an in-depth look into the system architecture, emphasizing security-related components to ensure a secure and efficient infrastructure.
Components:
- Deployment Models: Multi-tenant cloud-hosted and customer-hosted (on-premises) architectures.
- Detailed Architecture Diagram: Including security layers.
- AWS Amplify Configuration: Hosting, authentication, APIs, etc.
- Supporting Services: AWS Cognito for authentication, Amazon S3 for storage, etc.
5.1 Detailed Architecture Diagram
The security layers within the architecture of Sheetloom are structured to provide robust protection and efficient data management:
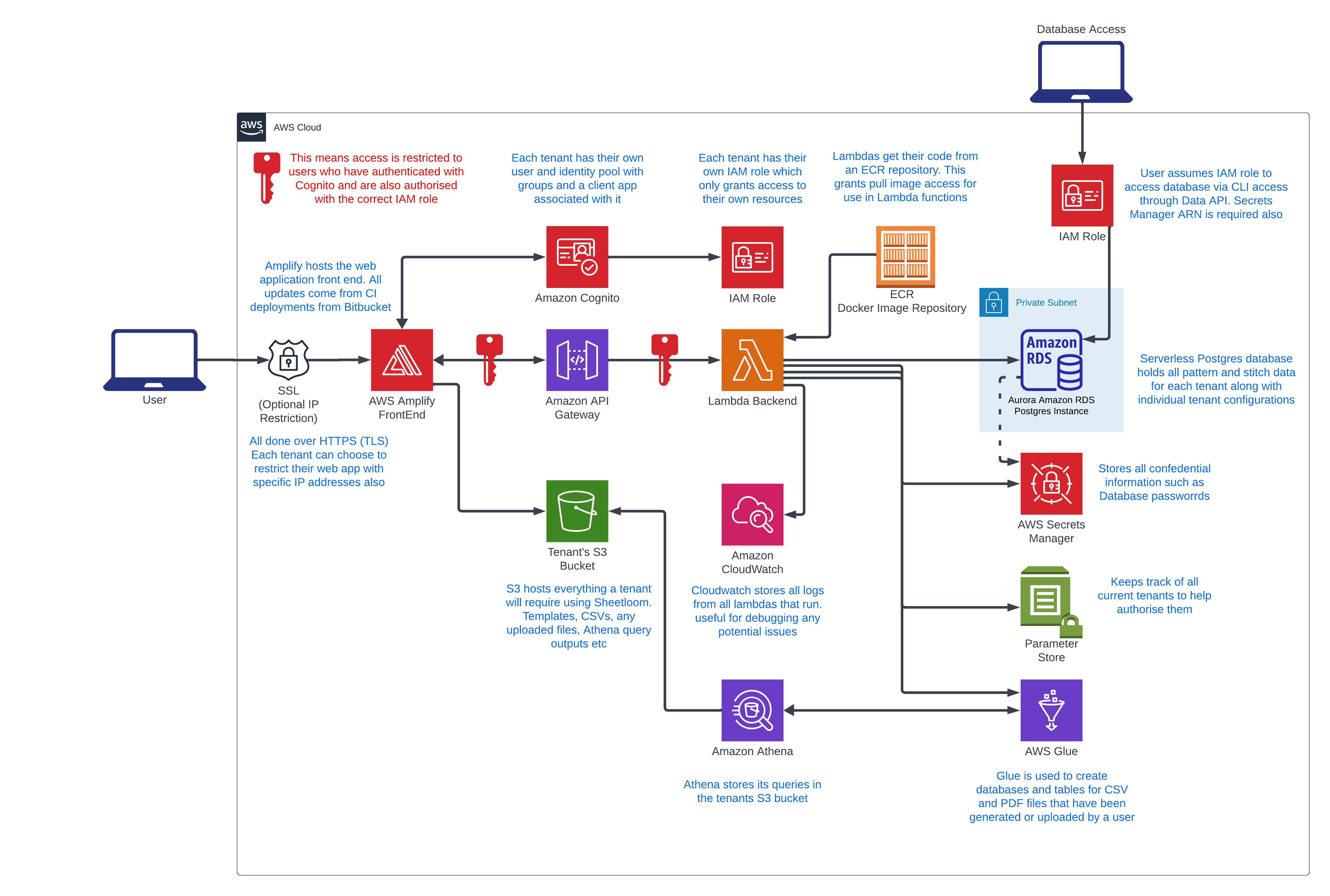
5.1.1 Multi-Tenant Cloud-Hosted Architecture
- Client Interaction:
- Users access Sheetloom via their company's secure subdomain
- Authentication through tenant-specific Cognito User Pool
- Secure token-based authentication (JWT) or client credentials for API access
- Authentication and Authorization:
- Each tenant has a dedicated Cognito User Pool and Identity Pool
- Temporary AWS credentials are scoped to tenant resources
- Role-based access control within each tenant environment
- Custom Lambda authorizer validates tokens and client credentials
- API Layer:
- API Gateway routes requests to appropriate Lambda functions
- Each request is authenticated and authorized before processing
- Lambda functions enforce tenant isolation and business logic
- Data Storage and Processing:
- Tenant data stored in isolated S3 buckets
- Shared Aurora PostgreSQL Serverless v1 cluster (version 13.9) stores metadata
- Glue manages metadata for tenant databases
- Athena enables secure SQL queries on tenant data
- Secrets Management:
- Secure storage of database credentials and API keys in AWS Secrets Manager
- Access limited to authorized services
- Networking:
- Shared VPC configuration with public and private subnets
- Security Groups and NACLs control traffic flow
- ECR hosts Lambda container images securely
- Automated Updates:
- EventBridge monitors ECR image updates
- Lambda refresher function automatically updates Lambda functions when new images are available
5.1.2 Customer-Hosted (On-Premises) Architecture
- Client Interaction:
- Users access Sheetloom via customer-managed domain or AWS Amplify URL
- Authentication through tenant-specific Cognito User Pool in customer's account
- Secure token-based authentication (JWT) or client credentials for API access
- Authentication and Authorization:
- Dedicated Cognito User Pool and Identity Pool per customer deployment
- Temporary AWS credentials are scoped to customer-specific resources
- Role-based access control within customer environment
- Custom Lambda authorizer validates tokens and client credentials
- API Layer:
- API Gateway routes requests to appropriate Lambda functions
- Each request is authenticated and authorized before processing
- Lambda functions enforce tenant isolation and business logic
- Data Storage and Processing:
- Customer-specific S3 bucket for data storage
- Dedicated Aurora PostgreSQL Serverless v2 cluster (version 15.8) in customer's account
- Glue manages metadata for customer databases
- Athena enables secure SQL queries on customer data
- Secrets Management:
- Secure storage of database credentials and API keys in customer's AWS Secrets Manager
- Access limited to authorized services within customer's account
- Networking:
- Customer-managed VPC configuration with public and private subnets
- Security Groups and NACLs configured per customer requirements
- Bastion host provides secure database access
- ECR images pulled from Sheetloom's core account but executed in customer account
- Automated Updates:
- EventBridge receives notifications from Sheetloom's core account when new images are available
- Lambda refresher function automatically updates Lambda functions when new images are pushed
- Customer maintains control over update timing and approval
5.2 AWS Amplify Configuration
- Hosting:
- Frontend hosted on AWS Amplify
- CloudFront distribution for content delivery
- Tenant-specific subdomains
- Authentication:
- Cognito User Pools for tenant authentication
- Identity Pools for AWS service access
- APIs:
- Secure API Gateway integration
- Lambda function routing
- Request authentication and authorization
5.3 Supporting Services Configuration
- AWS Cognito:
- Tenant-specific authentication
- Scoped AWS credentials
- Role-based access control
- Amazon S3:
- Isolated tenant buckets
- Encrypted data storage
- Access controls per tenant
- AWS Lambda:
- Serverless processing
- Tenant context isolation
- Least privilege access
- AWS Glue & Amazon Athena:
- Tenant database management
- Secure query execution
- Data access controls
- AWS Secrets Manager:
- Secrets are encrypted using AWS KMS and access-controlled, ensuring that only authorized services can retrieve sensitive information.
- Virtual Private Cloud (VPC):
- The VPC is divided into private and public subnets, with Security Groups and Network ACLs tailored to restrict unnecessary traffic and protect backend services.
- Elastic Container Registry (ECR):
- Container images are stored securely with access controls, preventing unauthorized modifications and ensuring that only trusted images are deployed.
6. Data Protection
Purpose:
Detail the mechanisms in place to secure data both at rest and in transit, ensuring comprehensive protection of sensitive information.
Components:
- Encryption at Rest: Utilizing AWS services' encryption capabilities to protect stored data.
- Encryption in Transit: Implementing TLS/SSL to secure data transmission.
- Data Classification: Categorizing data based on sensitivity to apply appropriate security controls.
- Data Lifecycle Management: Managing data from creation to deletion to maintain security and compliance.
6.1 Encryption at Rest
- Amazon S3:
- All tenant data stored in S3 buckets is encrypted using AES-256 encryption.
- Bucket Policies enforce encryption requirements, ensuring that all objects are stored securely without exceptions.
- Amazon RDS:
- Data stored in RDS Aurora PostgreSQL clusters is encrypted at rest using AWS-managed KMS keys
- Encryption is enabled by default for all Aurora clusters
- Database connections use SSL/TLS encryption for data in transit
- AWS Secrets Manager:
- Secrets are encrypted at rest using AWS Key Management Service (KMS) keys, safeguarding sensitive credentials and API keys.
6.2 Encryption in Transit
- TLS/SSL:
- All data transmitted between clients and Sheetloom is encrypted using TLS 1.2 or higher
- AWS Amplify and API Gateway enforce secure communication channels
6.3 Data Classification
| Level | Classification | Description | Examples | Security Requirements |
|---|---|---|---|---|
| 1 | Public | Information that can be freely shared |
|
|
| 2 | Internal | Information for internal use only |
|
|
| 3 | Confidential | Sensitive business information |
|
|
| 4 | Restricted | Highly sensitive information |
|
|
6.4 Data Lifecycle Management
- Data Storage:
- Tenant data is stored in dedicated S3 buckets with appropriate lifecycle policies
- Data Archiving:
- Older data is transitioned to S3 Glacier based on tenant requirements
- Data Deletion:
- Data retention policies ensure compliance requirements are met
- Secure deletion procedures for tenant termination
7. Identity and Access Management (IAM)
Purpose:
Describe how users and services are authenticated and authorized, ensuring that access is granted appropriately and securely.
Components:
- User Authentication: AWS Cognito configurations, MFA usage.
- Role-Based Access Control (RBAC): Permissions assigned to different roles.
- Least Privilege Principle: Ensuring users have only necessary access.
- Third-Party Access: How external services or partners access the application.
7.1 User Authentication
AWS Cognito Configuration:
- Each tenant has its own Cognito User Pool and Identity Pool
- Users authenticate via their tenant-specific subdomain
- MFA is available and can be enabled for user accounts
Multi-Factor Authentication (MFA):
- Time-based one-time passwords (TOTP)
- SMS-based verification codes
- Authenticator app support
Authentication Methods:
- JWT Token Authentication: Users authenticate using Cognito ID tokens or access tokens, which are validated by a custom API Gateway authorizer that verifies token signatures, expiration, and tenant claims.
- Client ID/Secret Authentication: Machine-to-machine (M2M) authentication is supported using client credentials stored securely in AWS Secrets Manager. This enables automated workflows and API integrations without user interaction.
- Token Validation: All tokens are validated against Cognito's public keys (JWKS), ensuring tokens are authentic and have not been tampered with. Token expiration and audience claims are strictly enforced.
7.2 Role-Based Access Control (RBAC)
- Defined Roles:
- Admin: Possesses full access to tenant-specific resources, including user management, data configurations, and system settings.
- User: Has limited access, primarily to interact with their own data, generate reports, and perform standard operational tasks.
- Permissions:
- Roles are defined with specific IAM policies that grant only the necessary permissions required for their functions.
- Admins can manage user accounts, configure data sources, oversee data processing tasks, and access all data within their tenant's scope.
- Users can access and manipulate their own data, generate and view reports, and perform tasks within the constraints of their IAM roles.
7.3 Least Privilege Principle
- Access Restrictions:
- Users are granted the minimal set of permissions required to perform their tasks, reducing the risk of unauthorized access or actions.
- Temporary AWS credentials issued via Cognito Identity Pools are scoped to specific resources, such as tenant-specific S3 buckets and related services, ensuring users cannot access resources outside their purview.
- IAM Policy Enforcement:
- Strict IAM policies prevent privilege escalation
- Regular policy reviews and audits
- Automated compliance checks
7.4 Third-Party Access
- External Services:
- Access for third-party services or partners is managed through dedicated IAM roles and policies, ensuring that external entities have only the access they require.
- API Gateway secures endpoints, allowing access only to authenticated and authorized third-party entities based on predefined access controls.
- Secure Integration:
- Third-party integrations utilize AWS Secrets Manager to handle API keys and credentials securely, preventing unauthorized access.
- Access is continuously monitored and logged to detect and prevent unauthorized activities, maintaining a secure integration environment.
8. Network Security
Purpose:
Detail the measures taken to protect the network infrastructure, ensuring secure communication channels and preventing unauthorized access.
Components:
- VPC Configuration: Virtual private cloud settings.
- Security Groups and NACLs: Rules governing inbound and outbound traffic.
- API Security: How APIs are secured.
- Amplify Security Features: Built-in security measures provided by AWS Amplify.
8.1 VPC Configuration
- Virtual Private Cloud (VPC):
- The application operates within a dedicated VPC, ensuring network isolation and security.
- Subnets:
- Public Subnets: Hosts API Gateway for external access, allowing secure and controlled inbound traffic.
- Private Subnets: Contains RDS metadata database, and other backend services, shielded from direct internet access to enhance security.
- Routing:
- Configured with appropriate route tables to manage traffic flow between subnets and internet gateways, ensuring that only necessary traffic is allowed.
8.2 Security Groups and Network ACLs (NACLs)
- Security Groups:
- Stateful firewall rules at the instance level
- Configured to allow only necessary traffic
- Regular audits of security group rules
- Network ACLs:
- Stateless network filtering at the subnet level
- Additional layer of network security
- Default deny-all with explicit allow rules
8.3 API Security
- API Gateway Configuration:
- Custom Lambda Authorizer:
- All API requests are authenticated through a custom Lambda authorizer that validates JWT tokens or client credentials
- The authorizer verifies token signatures using Cognito's public keys (JWKS), checks token expiration, validates audience and issuer claims, and enforces tenant isolation
- Client ID/Secret authentication is validated against credentials stored in AWS Secrets Manager
- Tenant ID validation ensures users can only access resources within their assigned tenant
- Authorization:
- Integrated with AWS Cognito to authenticate API requests, ensuring that only authorized users and services can access API endpoints
- Utilizes IAM roles and policies to authorize access to specific API endpoints based on user roles and permissions
- Role-based access control (RBAC) is enforced through Cognito user attributes and IAM role mappings
- Custom Lambda Authorizer:
- Rate Limiting and Throttling:
- Configured to prevent abuse and ensure fair usage by setting limits on the number of requests per second, mitigating the risk of Denial-of-Service (DoS) attacks.
- Input Validation:
- Implemented within Lambda functions to validate and sanitize incoming data, mitigating injection attacks and other vulnerabilities by ensuring that only properly formatted and expected data is processed.
8.4 AWS Amplify Security Features
Built-in Protection:
- DDoS protection through AWS Shield
- SSL/TLS certificate management
- Secure content delivery
Rules and Protections:
- SQL Injection and Cross-Site Scripting (XSS) Protection: Automated rules detect and block malicious payloads targeting database queries and client-side scripts.
- IP Blacklisting/Whitelisting: Restrict access based on IP addresses to block known malicious sources and allow trusted entities.
- Rate-Based Rules: Automatically block IPs that exceed predefined request thresholds, preventing Distributed Denial-of-Service (DDoS) attacks and ensuring application availability.
Security Best Practices:
- Automated security patches
- Secure hosting configuration
- Protection against common web vulnerabilities
9. Monitoring and Logging
Purpose:
Explains how the application's security is monitored and how logs are managed to ensure visibility, accountability, and timely detection of security incidents.
Components:
- Logging Services: AWS CloudWatch, AWS CloudTrail configurations.
- Log Retention Policies: How long logs are stored and where.
- Monitoring Tools: Tools used for real-time monitoring and alerting.
- Incident Detection: Methods for identifying security incidents.
9.1 Logging Services
- AWS CloudWatch:
- Logs: Captures logs from Lambda functions and API Gateway, providing detailed insights into application behavior and performance.
- Metrics: Monitors performance metrics such as latency, error rates, and request counts, enabling proactive performance optimization and issue detection.
- AWS CloudTrail:
- Event Logging: Records API calls and actions taken within the AWS environment, providing a comprehensive audit trail for security analysis and compliance auditing.
- Integration: Logs are centralized and integrated with CloudWatch Logs for streamlined analysis and alerting, facilitating real-time monitoring and incident response.
9.2 Log Retention Policies
- Retention Durations:
- CloudWatch Logs: Retained for 90 days to facilitate troubleshooting, performance monitoring, and short-term audit requirements.
- CloudTrail Logs: Retained for one year to comply with audit and compliance requirements, ensuring long-term availability of historical event data.
- Storage Locations:
- Logs are stored in secure S3 buckets with strict access controls to ensure their integrity and confidentiality, preventing unauthorized access or tampering.
9.3 Monitoring Tools
- Real-Time Monitoring:
- AWS CloudWatch Dashboards: Provide visual representations of key metrics and system health indicators, offering an at-a-glance view of application performance and security status.
- CloudWatch Alarms: Trigger notifications based on predefined thresholds for metrics like CPU usage, memory consumption, and error rates, enabling prompt response to potential issues.
- Alerting Mechanisms:
- Amazon SNS (Simple Notification Service): Sends alerts via email, SMS, or other protocols to notify relevant personnel of critical events or anomalies, ensuring timely awareness and action.
9.4 Incident Detection
- Automated Detection:
- CloudWatch Alarms: Automatically detect and notify about unusual patterns or potential security incidents, facilitating swift identification and response.
- Manual Monitoring:
- Security Team Oversight: Regularly reviews logs and monitoring dashboards to identify and investigate suspicious activities, complementing automated detection with human analysis.
10. Incident Response
Purpose:
Outline the procedures for responding to security incidents, ensuring a structured and effective approach to managing and mitigating threats.
Components:
- Incident Detection: How incidents are identified.
- Response Plan: Steps to take when an incident occurs.
- Roles and Responsibilities: Who is responsible for each part of the response.
- Communication Plan: How to communicate internally and externally during incidents.
10.1 Incident Detection
- Monitoring Systems:
- AWS CloudWatch and AWS CloudTrail continuously monitor and log activities within the application, providing real-time visibility into system operations and potential security events.
- Automated Alerts:
- CloudWatch Alarms and Amazon GuardDuty automatically detect and notify about potential security incidents, enabling swift identification and response.
- Manual Reporting:
- Users and team members can report suspicious activities or security concerns through a designated internal communication channel, ensuring that all potential threats are promptly addressed.
10.2 Response Plan
- Initial Assessment:
- Verify the incident and assess its impact
- Classify the incident severity
- Containment:
- Isolate affected systems to prevent further damage
- Implement temporary fixes
- Eradication:
- Identify the root cause
- Remove malicious components
- Recovery:
- Restore systems to normal operation
- Monitor for any signs of recurrence
- Post-Incident Review:
- Conduct a thorough review to identify lessons learned
- Update response plans and security measures
10.3 Roles and Responsibilities
- Incident Response Team:
- Security Lead: Oversees the incident response process and coordinates efforts across teams, ensuring a unified and effective response.
- System Administrators: Handle technical aspects of containment, eradication, and recovery, restoring system functionality and security.
- Developers: Assist in identifying and fixing vulnerabilities in the application, ensuring that code-level issues are addressed.
- Communications Officer: Manages internal and external communications during the incident, maintaining transparency and trust.
10.4 Communication Plan
- Internal Communication:
- Immediate Notifications: Use internal channels, such as Teams or Slack, to alert the incident response team and relevant stakeholders, ensuring that all necessary parties are informed promptly.
- External Communication:
- Regulatory Notifications: Comply with GDPR requirements by notifying supervisory authorities and affected individuals within the mandated timeframe if personal data is compromised, ensuring legal compliance and transparency.
- Public Statements: Issue official statements as necessary to inform users and the public about the incident and remedial actions taken, maintaining trust and credibility.
- Communication Tools:
- Utilize secure communication platforms to ensure that sensitive information about the incident is shared only with authorized personnel, preventing information leakage and maintaining confidentiality.
11. Third-Party Services and Dependencies
Purpose:
Identify and assess the security of third-party services integrated with the application to ensure that external dependencies do not introduce vulnerabilities or compliance issues.
Components:
- List of Third-Party Services: APIs, libraries, plugins, etc.
- Security Assessments: Evaluations or audits of third-party services.
- Dependency Management: How dependencies are managed and updated.
11.1 List of Third-Party Services
11.1.1 Libraries and Frameworks
Frontend Libraries:
- Bootstrap (
^5.3.0):- Description: Frontend framework for developing responsive and mobile-first websites, ensuring a consistent and user-friendly interface.
- Bootstrap Icons (
^1.10.5):- Description: Official open-source SVG icon library for Bootstrap, providing a wide range of scalable icons for enhancing UI components.
- Datatables.net-bs5 (
^1.13.6), Datatables.net-responsive-bs5 (^2.5.0), Datatables.net-select-bs5 (^1.7.0):- Description: jQuery-based plugins for creating dynamic and interactive tables with Bootstrap 5 styling, enabling advanced data presentation and manipulation features.
- Vanillajs-datepicker (
^1.3.4):- Description: Lightweight and dependency-free datepicker for vanilla JavaScript, facilitating user-friendly date selection in forms and reports.
- jQuery (
^3.7.0), jQuery-ExtendExt (^1.0.0), jQuery-UI (^1.13.2):- Description: JavaScript libraries for DOM manipulation, event handling, and creating interactive UI components, enhancing the application's frontend interactivity and responsiveness.
Backend Libraries:
- AWS Amplify (
^5.2.5):- Description: JavaScript library for interfacing with AWS services, facilitating seamless integration between frontend and backend components.
- AWS SDK (
^2.1420.0):- Description: Collection of tools for interacting with various AWS services, enabling programmatic management and integration within the application.
- Knex (
^3.1.0):- Description: SQL query builder for Node.js, supporting multiple database engines and simplifying database interactions.
- pg (
^8.11.5):- Description: PostgreSQL client for Node.js, facilitating efficient communication with PostgreSQL databases.
- AWS Lambda Dependencies:
- axios: Promise-based HTTP client for the browser and Node.js, enabling efficient API requests and data fetching.
- lodash: Utility library delivering modularity, performance, and extras, simplifying JavaScript development.
- jsonwebtoken: Implementation of JSON Web Tokens, facilitating secure token-based authentication and authorization.
- dotenv: Loads environment variables from a
.envfile intoprocess.env, enabling secure and flexible configuration management.
Utility Libraries:
- moment (
^2.30.1):- Description: Library for parsing, validating, manipulating, and formatting dates, simplifying date and time operations.
- date-fns (
^3.6.0):- Description: Modern JavaScript date utility library, providing a comprehensive set of functions for date manipulation.
- mathjs (
^13.0.2):- Description: Extensive math library for JavaScript and Node.js, supporting complex mathematical operations and calculations.
- handlebars (
^4.7.8):- Description: Templating engine for generating dynamic HTML, enabling flexible and reusable frontend components.
- interactjs (
^1.10.17):- Description: JavaScript library for drag and drop, resizing, and multi-touch gestures, enhancing frontend interactivity and user experience.
- assert (
^2.0.0), jsdom (^22.1.0), jsonpath (^1.1.1), jsonpath-plus (^7.2.0), JSV (^4.0.2), sql-parser-mistic (^1.2.3), node-sql-parser (^4.17.0):- Description: Various utility libraries for assertions, DOM manipulation, JSON querying, validation, and SQL parsing, supporting diverse backend functionalities.
- pako (
^2.1.0):- Description: Fast zlib port to JavaScript, primarily for data compression, optimizing data storage and transmission.
- papaparse (
^5.4.1):- Description: Powerful CSV parser for JavaScript, enabling efficient parsing and manipulation of CSV data.
- underscore (
^1.13.6):- Description: Utility-belt library for JavaScript that provides support for the usual functional suspects, enhancing code readability and efficiency.
Build and Development Tools:
- parcel (
latest), parcel-reporter-static-files-copy (^1.5.0):- Description: Blazing fast, zero-configuration web application bundler, streamlining the build process and optimizing frontend assets.
- babel-plugin-closure-elimination (
^1.3.2), babel-plugin-transform-remove-console (^6.9.4):- Description: Babel plugins for optimizing and cleaning up the code during the build process, enhancing performance and security by eliminating unnecessary code and console statements.
- typescript (
^5.1.6):- Description: Superset of JavaScript that compiles to clean JavaScript output, enabling strong typing and improved developer productivity.
- aws-amplify (
^5.2.5):- Description: Frontend library to interact with AWS services like Cognito, S3, etc., facilitating seamless integration and efficient development workflows.
11.1.2 Plugins
- Chart.js Plugin:
- Description: Utilized for rendering interactive charts and graphs, providing visual representations of data to enhance reporting and analytics.
- ExcelJS Plugin:
- Description: Employed for generating and manipulating Excel spreadsheets, enabling the creation of customized and dynamic reports based on tenant-specific data.
11.2 Security Assessments
- Vendor Evaluations:
- Process: Conduct due diligence on all third-party vendors to ensure they adhere to robust security practices and compliance standards.
- Criteria: Evaluate based on factors such as security certifications (e.g., SOC 2, ISO 27001), history of vulnerabilities, responsiveness to security incidents, and overall reputation within the industry.
- Regular Audits:
- Frequency: Perform regular security audits of all third-party services and libraries, ensuring that they continue to meet security and compliance requirements.
- Scope: Assess the security posture, update frequency, community support, and vulnerability management practices of each dependency to identify and mitigate potential risks.
- Vulnerability Scanning:
- Tools Used: Utilize tools like Snyk, Dependabot, and npm audit to scan dependencies for known vulnerabilities.
- Procedure:
- Automatically scan for vulnerabilities as part of the CI/CD pipeline to ensure continuous monitoring.
- Review and address any reported issues promptly by updating or replacing vulnerable packages, maintaining the application's security integrity.
- Risk Assessment for Dependencies:
- Assessment: Evaluate the potential risks associated with each third-party library or service, considering factors such as the library's maintenance status, popularity, and historical security incidents.
- Mitigation: Implement measures such as restricting usage of high-risk libraries, limiting their access within the application, and ensuring that only actively maintained and secure dependencies are incorporated into the project.
11.3 Dependency Management
- Version Control:
- Strategy: Maintain up-to-date versions of all libraries and frameworks to incorporate security patches and improvements, reducing the risk of vulnerabilities.
- Implementation: Use package.json and package-lock.json to manage and lock dependency versions, ensuring consistency across development, staging, and production environments.
- Automated Updates:
- Tools Used: Implement automated dependency management tools such as Dependabot, Renovate, and npm audit to streamline the update process.
- Functionality: Automatically monitor dependencies for updates and security patches, and create pull requests to apply these updates, ensuring that the application remains secure and up-to-date.
- Review Processes:
- Code Reviews: Incorporate dependency changes into the regular code review process to assess the impact and security implications of updates, ensuring that updates do not introduce new vulnerabilities or conflicts.
- Testing: Ensure that updates do not introduce regressions by running comprehensive tests, including unit tests, integration tests, and end-to-end tests, before deployment.
- Minimal Dependency Principle:
- Approach: Limit the number of third-party dependencies to those that are essential for application functionality, reducing the potential attack surface and minimizing the risk of introducing vulnerabilities.
- Benefit: A lean dependency tree enhances the application's security posture by decreasing the likelihood of security flaws and simplifying maintenance.
- Documentation:
- Record Keeping: Maintain detailed documentation of all third-party dependencies, including their purpose, version, source, and any known vulnerabilities, facilitating transparency and accountability.
- Change Logs: Keep track of changes to dependencies over time to facilitate auditing, troubleshooting, and understanding the evolution of the application's security landscape.
11.4 Best Practices for Managing npm Dependencies
- Lockfile Maintenance:
- Usage: Use
package-lock.jsonto lock the versions of dependencies, ensuring consistent installations across different environments and preventing unintended updates that could introduce vulnerabilities.
- Usage: Use
- Semantic Versioning Awareness:
- Understanding: Be aware of semantic versioning (major.minor.patch) to predict the impact of updates, understanding that major version changes may introduce breaking changes.
- Policy: Avoid automatic major version upgrades without thorough testing to ensure that updates do not disrupt application functionality or security.
- Audit and Remediation:
- Regular Audits: Schedule regular audits using
npm auditto identify and fix vulnerabilities, ensuring that dependencies remain secure and compliant. - Immediate Action: Prioritize fixing high-severity vulnerabilities immediately to prevent exploitation and maintain the application's security integrity.
- Regular Audits: Schedule regular audits using
- Transitive Dependencies Monitoring:
- Awareness: Recognize that dependencies of your dependencies (transitive dependencies) can also introduce vulnerabilities, necessitating comprehensive monitoring.
- Tools: Use tools like Snyk and npm audit that can detect vulnerabilities in transitive dependencies, ensuring that all layers of the dependency tree are secure.
- Secure Coding Practices:
- Validation: Validate and sanitize all inputs and outputs when using third-party libraries to prevent injection attacks and other security vulnerabilities.
- Configuration: Properly configure libraries to minimize security risks, such as disabling unnecessary features or services, and adhering to best practices for secure configuration.
11.5 Summary
Proper management and assessment of third-party services and dependencies, including npm-installed libraries, are vital for maintaining the security and integrity of the Sheetloom application. By adhering to the practices outlined above, you can mitigate risks associated with external dependencies, ensure that all integrated services are secure and compliant, and maintain a robust and resilient application environment.
12. Deployment and Configuration Management
Purpose:
Detail the deployment processes and configuration management practices that ensure secure and consistent application updates.
Components:
- Deployment Process: How code changes are deployed securely.
- Environment Management: How different environments are maintained.
- Configuration Security: How sensitive configurations are protected.
12.1 Deployment Process
Frontend Deployment:
- AWS Amplify automatically triggers deployments based on BitBucket branch updates:
devbranch → Development environmentpreprodbranch → Pre-production environmentprodbranch → Production environment
- Each deployment includes:
- Automated build process
- Asset optimization
- Content delivery configuration
- AWS Amplify automatically triggers deployments based on BitBucket branch updates:
Backend Deployment - Multi-Tenant (Cloud-Hosted):
Docker Image Management (
run_ecr_build.sh):- Automates the build process for all Lambda function Docker images
- Handles deployment of images to corresponding ECR repositories
- Manages ECR permissions and access controls
- Ensures consistent container environments across all functions
Infrastructure Management (
sam.sh):Handles CloudFormation and AWS SAM template deployments
Manages distinct YAML configuration files:
template_local.yaml:
- Configured for local development and testing
- Enables developers to test changes in isolated environment
template_root.yaml:
- Creates and manages core AWS services
- Handles multi-tenant infrastructure setup
- Establishes foundational services for Sheetloom
- Deploys shared Aurora PostgreSQL Serverless v1 cluster
template_mt.yaml:
- Environment-specific configurations (dev, preprod, prod)
- Manages API Gateway setup and configuration
- Handles Lambda function deployment for each environment
- Uses EventBridge to automatically refresh Lambda functions when ECR images are updated
Backend Deployment - Customer-Hosted (On-Premises):
Deployment Script (
sheetloom-on-prem-deploy.sh):- Automates the complete deployment process in customer AWS accounts
- Creates tenant-specific AWS Amplify app for frontend hosting
- Sets up isolated VPC with public and private subnets
- Deploys dedicated Aurora PostgreSQL Serverless v2 cluster (provisioned mode)
- Creates tenant-specific Cognito User Pool and Identity Pool
- Configures API Gateway with custom Lambda authorizer
- Sets up EventBridge rules to monitor ECR image updates from Sheetloom's core account
- Automatically refreshes Lambda functions when new container images are available
Infrastructure Template (
template_on_prem.yaml):- Specialized for customer AWS account deployments
- Production-only environment configuration
- Utilizes Docker images from Sheetloom's core AWS account (via cross-account ECR access)
- Creates isolated infrastructure per customer:
- Dedicated VPC with bastion host for database access
- Tenant-specific RDS Aurora PostgreSQL cluster (version 15.8)
- Tenant-specific S3 bucket for data storage
- Tenant-specific Cognito pools for authentication
- Tenant-specific API Gateway and Lambda functions
- Implements EventBridge integration to receive ECR image update notifications from Sheetloom's core account
- Ensures complete tenant isolation within customer's AWS account
Security Considerations for Customer-Hosted Deployments:
- All infrastructure is deployed in the customer's AWS account, providing complete data sovereignty
- Customer maintains full control over network security, IAM policies, and compliance configurations
- Docker images are pulled from Sheetloom's ECR but run entirely within customer's account
- Database credentials are managed through AWS Secrets Manager in the customer's account
- EventBridge rules allow Sheetloom's core account to notify customer deployments of image updates, but customer controls when to apply updates
12.2 Environment Management
- Development Environment:
- Triggered by changes to
devbranch - Used for active development and testing
- Contains non-sensitive test data
- Triggered by changes to
- Pre-production Environment:
- Triggered by changes to
preprodbranch - Mirrors production configuration
- Used for final testing before production release
- Triggered by changes to
- Production Environment:
- Triggered by changes to
prodbranch - Hosts live application
- Contains customer data
- Deployment requires additional approval steps
- Triggered by changes to
12.3 Configuration Security
- Sensitive Information:
- API keys stored in AWS Secrets Manager
- Database credentials managed through IAM roles
- Environment variables secured in Lambda configurations
- Access Controls:
- Production configurations restricted to authorized personnel
- Changes require approval and documentation
- Regular audits of configuration access
- Deployment Security:
- Backend deployment scripts maintained in version control
- Access to ECR and Lambda updates restricted to authorized team members
- CloudFormation changes reviewed before application
13. Risk Assessment and Management
Purpose:
Outline the framework and processes for identifying, assessing, and managing security risks to the application.
13.1 Risk Assessment Framework
| Component | Description |
|---|---|
| Likelihood | 1 (Rare) to 5 (Almost Certain) |
| Impact | 1 (Negligible) to 5 (Critical) |
| Risk Score | Likelihood × Impact |
| Risk Level | Low (1-6), Medium (7-14), High (15-19), Critical (20-25) |
13.2 Risk Analysis Matrix
| Risk Score | 1-6 | 7-14 | 15-19 | 20-25 |
|---|---|---|---|---|
| Category | Low | Medium | High | Critical |
| Review Frequency | Annual | Quarterly | Monthly | Weekly |
| Owner Level | Team Lead | Department Head | CTO/CISO | Executive Team |
13.3 Identified Risks
13.3.1 Technical Risks
| Risk ID | Description | Likelihood | Impact | Score | Controls |
|---|---|---|---|---|---|
| TR-01 | Data breach via unauthorized access | 3 | 5 | 15 |
|
| TR-02 | Service disruption due to AWS outage | 2 | 4 | 8 |
|
| TR-03 | Data loss due to backup failure | 2 | 5 | 10 |
|
| TR-04 | API rate limiting breach | 3 | 3 | 9 |
|
| TR-05 | Dependency vulnerability exploit | 4 | 4 | 16 |
|
13.3.2 Operational Risks
| Risk ID | Description | Likelihood | Impact | Score | Controls |
|---|---|---|---|---|---|
| OR-01 | Human error in production deployment | 3 | 4 | 12 |
|
| OR-02 | Insufficient incident response | 2 | 4 | 8 |
|
| OR-03 | Key personnel dependency | 3 | 4 | 12 |
|
| OR-04 | Configuration management errors | 3 | 3 | 9 |
|
13.3.3 Compliance Risks
| Risk ID | Description | Likelihood | Impact | Score | Controls |
|---|---|---|---|---|---|
| CR-01 | GDPR compliance violation | 2 | 5 | 10 |
|
| CR-02 | SOC 2 requirements breach | 2 | 4 | 8 |
|
| CR-03 | Data retention violation | 3 | 4 | 12 |
|
13.4 Risk Treatment Plans
High and Critical Risks (Score ≥ 15)
TR-01: Data Breach Prevention
- Implementation Timeline: Q2 2024
- Budget Allocation: $XXX,XXX
- Actions:
- Implement advanced threat detection
- Enhance access controls
- Regular penetration testing
- Security awareness training
TR-05: Dependency Management
- Implementation Timeline: Q3 2024
- Budget Allocation: $XX,XXX
- Actions:
- Implement automated dependency updates
- Establish vulnerability management program
- Regular security assessments
- Vendor security reviews
13.5 Risk Monitoring and Review
13.5.1 Monitoring Metrics
Technical Metrics
- Security incident frequency
- Mean time to detect (MTTD)
- Mean time to resolve (MTTR)
- Vulnerability closure rate
Operational Metrics
- System availability
- Deployment success rate
- Incident response time
- Training completion rate
Compliance Metrics
- Audit findings
- Policy violations
- Compliance training completion
- Control effectiveness
13.5.2 Review Schedule
| Risk Level | Review Frequency | Stakeholders | Deliverables |
|---|---|---|---|
| Critical | Weekly | Executive Team | Status Report |
| High | Monthly | Security Team | Risk Assessment |
| Medium | Quarterly | Department Heads | Trend Analysis |
| Low | Annual | Team Leads | Summary Report |
13.6 Risk Appetite Statement
Sheetloom maintains a balanced approach to risk management:
Zero Tolerance
- Customer data breaches
- Regulatory compliance violations
- Extended service outages
Moderate Tolerance
- Minor service disruptions
- Non-critical feature delays
- Performance degradation
Risk Accepting
- New technology adoption
- Feature experimentation
- Process improvements
13.7 Annual Risk Assessment Schedule
| Month | Activity | Participants | Deliverables |
|---|---|---|---|
| January | Annual Risk Review | All Stakeholders | Annual Report |
| April | Q1 Assessment | Security Team | Quarterly Update |
| July | Mid-year Review | Department Heads | Mid-year Report |
| October | Q3 Assessment | Security Team | Quarterly Update |
13.8 Risk Management Roles and Responsibilities
Executive Team
- Risk appetite definition
- Resource allocation
- Strategic direction
Security Team
- Risk assessment execution
- Control implementation
- Monitoring and reporting
Department Heads
- Risk identification
- Control effectiveness
- Team compliance
Team Members
- Risk reporting
- Control execution
- Process adherence
14. Physical Security
Purpose:
Detail the physical security measures protecting the infrastructure, ensuring that physical access is controlled and monitored to prevent unauthorized access and tampering.
Components:
- Data Center Security: Physical security controls for data centers, if managing own servers.
- Access Controls: Physical access to facilities and equipment.
Note:
For AWS services like Amplify, physical security is managed by AWS. This section outlines AWS's physical security measures and how they support Sheetloom's security posture.
14.1 AWS Physical Security
- AWS Compliance Certifications:
- AWS data centers comply with industry-leading physical security standards, including ISO 27001, SOC 2, and PCI-DSS, ensuring that physical infrastructure meets stringent security requirements.
- Data Center Protections:
- AWS employs multiple layers of physical security, including perimeter fencing, security guards, intrusion detection systems, and biometric access controls, to protect against unauthorized physical access and environmental threats.
14.2 Reference to AWS Security
- Shared Responsibility Model:
- While AWS manages the physical security of their data centers, Sheetloom is responsible for securing data and configurations within the AWS environment, adhering to best practices for data protection and access management.
- Compliance Alignment:
- Leverage AWS's compliance certifications, including AWS Amplify, to support Sheetloom's adherence to GDPR and other relevant regulations, ensuring that the underlying infrastructure meets necessary security and compliance standards.
15. Customer-Hosted Deployments
Purpose:
Detail the security considerations and architecture for Sheetloom deployments hosted in customer AWS accounts, ensuring customers understand the security model and their responsibilities.
Components:
- Deployment Model: How Sheetloom is deployed in customer AWS accounts.
- Security Isolation: How customer data and infrastructure are isolated.
- Update Management: How security updates and patches are delivered.
- Customer Responsibilities: Security responsibilities shared between Sheetloom and the customer.
15.1 Deployment Model
Sheetloom offers a customer-hosted deployment option where the entire application stack is deployed in the customer's own AWS account. This deployment model provides:
- Complete Data Sovereignty: All customer data remains within the customer's AWS account and region
- Enhanced Isolation: Complete infrastructure isolation from other tenants
- Customer Control: Full control over network security, compliance configurations, and access policies
- Compliance Alignment: Ability to align with customer-specific compliance requirements and data residency regulations
15.2 Infrastructure Components
Each customer-hosted deployment includes:
- Dedicated VPC: Isolated virtual network with public and private subnets
- Aurora PostgreSQL Cluster: Dedicated Aurora Serverless v2 cluster (version 15.8) with configurable capacity scaling
- S3 Bucket: Customer-specific bucket for template and data storage
- Cognito Pools: Dedicated User Pool and Identity Pool for customer authentication
- API Gateway: Customer-specific API endpoints
- Lambda Functions: All Lambda functions run in customer's account using container images from Sheetloom's ECR
- Bastion Host: EC2 instance for secure database access and administrative tasks
- Secrets Manager: Customer-managed secrets for database credentials and API keys
15.3 Security Isolation
- Network Isolation:
- Each deployment uses a dedicated VPC with customer-controlled security groups and network ACLs
- Database access is restricted to VPC-internal traffic and bastion host
- No network connectivity between customer deployments and Sheetloom's multi-tenant infrastructure
- Data Isolation:
- All customer data is stored in resources within the customer's AWS account
- Database clusters are dedicated per customer
- S3 buckets are customer-specific and isolated
- Access Control:
- IAM roles and policies are scoped to customer-specific resources
- Cognito pools are isolated per customer
- No cross-tenant access is possible
15.4 Update Management
- Container Image Updates:
- Lambda function container images are stored in Sheetloom's core AWS account ECR
- Customer deployments pull images from Sheetloom's ECR via cross-account access
- EventBridge rules enable Sheetloom to notify customer deployments when new images are available
- Automated Refresh:
- Lambda refresher function monitors EventBridge for ECR image update notifications
- When new images are detected, Lambda functions are automatically updated
- Customers can configure approval workflows or manual update processes if required
- Security Patches:
- Security patches and updates are delivered through new container images
- Customers receive notifications of available updates
- Update application is controlled by the customer
15.5 Customer Responsibilities
When deploying Sheetloom in their AWS account, customers are responsible for:
- Network Security:
- Configuring VPC security groups and network ACLs according to their security policies
- Managing bastion host access and key pairs
- Implementing network monitoring and intrusion detection as required
- IAM Management:
- Managing IAM roles and policies for their organization
- Implementing least privilege access controls
- Regular review and audit of IAM configurations
- Compliance:
- Ensuring deployment meets their organization's compliance requirements
- Configuring data retention and lifecycle policies
- Implementing audit logging and monitoring as required
- Update Management:
- Reviewing and approving security updates and patches
- Testing updates in non-production environments before applying to production
- Maintaining update schedules aligned with their change management processes
15.6 Sheetloom Responsibilities
Sheetloom maintains responsibility for:
- Application Security:
- Secure coding practices and vulnerability management
- Regular security assessments and penetration testing
- Timely delivery of security patches and updates
- Container Images:
- Maintaining secure and up-to-date container images in ECR
- Vulnerability scanning of container images
- Providing update notifications through EventBridge
- Documentation:
- Providing deployment guides and security documentation
- Maintaining change logs and release notes
- Supporting customer security assessments and audits
15.7 Shared Responsibility Model
The customer-hosted deployment follows AWS's shared responsibility model:
- AWS Responsibility: Physical security, infrastructure security, and managed service security
- Sheetloom Responsibility: Application security, secure container images, and update delivery
- Customer Responsibility: Network security, IAM management, compliance configuration, and update approval
This model ensures that security responsibilities are clearly defined and that customers maintain control over their security posture while benefiting from Sheetloom's secure application platform.
16. Conclusion
Purpose:
Summarize the security posture and reaffirm the commitment to maintaining and improving security, ensuring stakeholders are confident in the application's resilience and compliance.
Components:
- Summary of Security Measures: Recap key security controls.
- Future Plans: Upcoming security enhancements or reviews.
- Commitment Statement: Reiterate dedication to security and compliance.
This document outlines the comprehensive security measures implemented to protect the Sheetloom application across both multi-tenant cloud-hosted and customer-hosted deployment models. By leveraging AWS services such as Amplify, Cognito, S3, Aurora PostgreSQL, and Lambda, we ensure data confidentiality, integrity, and availability for our tenants. Our adherence to GDPR and alignment with industry standards like ISO/IEC 27001 and SOC 2 demonstrate our commitment to data privacy and regulatory compliance.
For multi-tenant deployments, we maintain strict tenant isolation and implement robust security controls to protect all customer data. For customer-hosted deployments, we provide complete infrastructure isolation within the customer's AWS account, enabling data sovereignty and enhanced control while maintaining the same high security standards.
We continuously monitor our systems, conduct regular security assessments, and update our practices to address emerging threats. Sheetloom remains dedicated to maintaining the highest standards of security and compliance to safeguard our users and their data, regardless of deployment model.